THE BEST CYBER-ATTACK SIMULATION PLATFORM
Cymulate is a SaaS cyber-attack simulation platform that allows to know and optimize the security level of an organization at any time continuously. With just a few clicks, Cymulate challenges security controls by performing thousands of attack simulations, quickly exposing security breaches and providing the corresponding mitigations, making security continuous, fast and part of the daily activity. The most complete BAS (Breach & Attack Simulation) solution on the market and the only one that simulates the entire attack vector.
The solution is structured in 10 attack vectors, where a vector is understood as a set of techniques, procedures and countermeasures that are executed to test part of the information infrastructure. Each vector has well-defined boundaries.
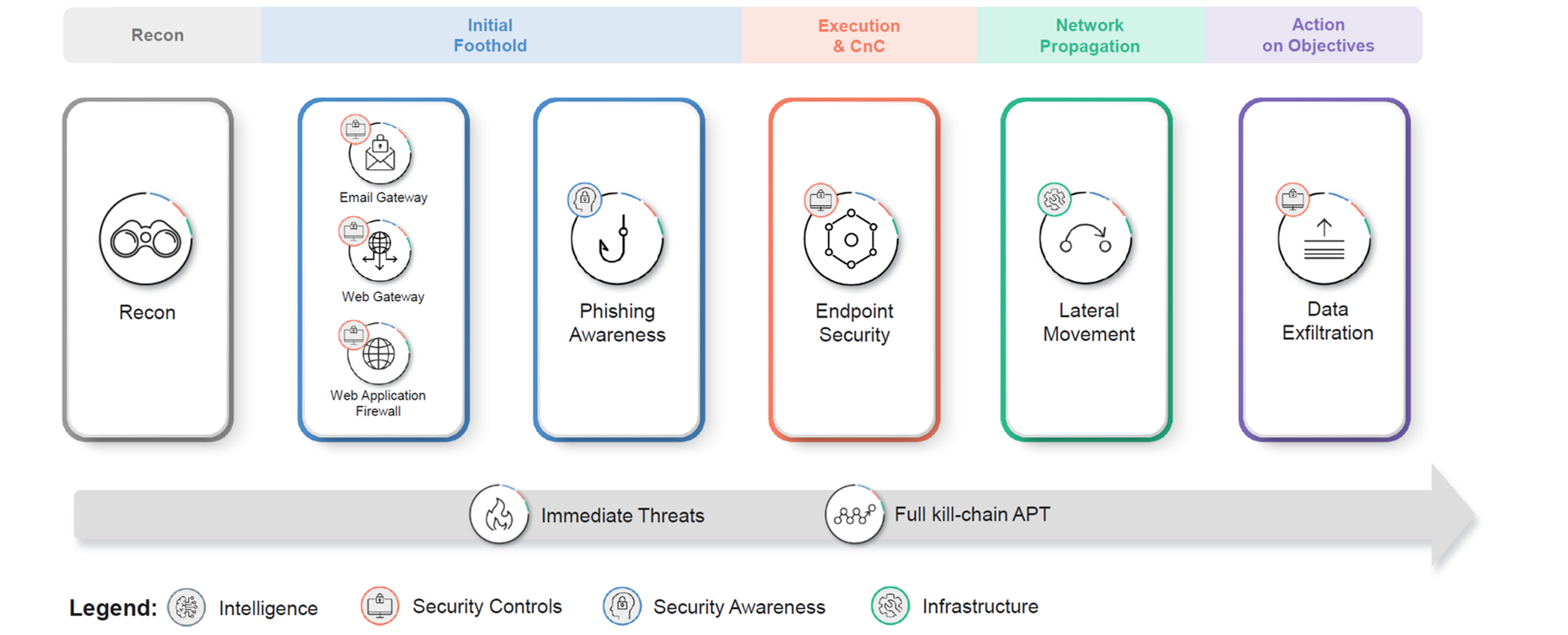
E-MAIL GATEWAY
The Email Gateway simulation vector is designed to assess your organization's email security and potential exposure to a series of malicious payloads sent via email. The simulated attack exposes critical vulnerabilities within the email security framework.
WEB GATEWAY
This vector tests outbound HTTP / HTTPS exposure to malicious websites using common HTTP / HTTPS protocols. The browser security tests are performed against a large and continuously growing database of malicious websites on the web.
WEB APPLICATION FIREWALL
This is the vector that tests WAF security for web payloads and better protection of your web applications. The WAF assessment will test your configuration, implementation and features, ensuring that it blocks common web application payloads before they approach your web application.
PHISHING AWARENESS
Allows you to test your employees' awareness of phishing campaigns by creating and executing simulated phishing campaigns. Helps you create training programs and strengthen your employees' behavior.
ENDPOINTS SECURITY
Allows organizations to deploy and run ransomware, Trojans, worms and virus simulations on a dedicated endpoint in a controlled and secure manner. Attack simulation determines whether your security products are tuned correctly and actually protect your organization's critical assets against the latest attack methods.
HOPPER - LATERAL MOVEMENT
Lateral movement in a Windows domain network is a common penetration scenario. This vector tests your Windows domain network configuration using a sophisticated algorithm that brings together all the common and dedicated techniques used to move within the network.
DATA EXFILTRATION (DLP)
It validates critical outbound data securely before exposing actual data. Our assessment allows you to test the outbound data flow to validate that your core assets remain within your organization.
IMMEDIATE THREAT INTELLIGENCE
Designed to inform and evaluate your organization's security posture as quickly as possible against the latest cyber-attacks. The simulation is created by the Cymulate Research Lab, which detects and analyzes threats immediately after they are launched by malicious cybercriminals and hackers.
RECON
Designed to search for information about the organization in a multitude of intelligence sources, both public and "pseudorestricted". It presents all the information found, using it as input for actions in the rest of the vectors.
FULL KILL-CHAIN APT
Cymulate's APT Full Kill-Chain simulation module provides a solution to the challenge of security effectiveness testing across the entire cyber kill chain by instrumenting your security framework in a comprehensive and easy-to-use manner.
"Security leaders should have a continuous security assessment posture regarding the highest risk threat vectors."
Gartner “How to Respond to the 2019 Threat Landscape,” Jeremy D’Hoinne, 16 August 2019

